Security Architecture
AWS Nitro Trusted Execution Environment
Core API leverages AWS Nitro TEE to provide hardware-level security for all cryptographic operations. This ensures that:- Private keys are never exposed in plaintext
- All cryptographic operations happen in an isolated, tamper-proof environment
- Even Magic cannot access your private keys without proper authorization
Key Sharding System
Core API uses advanced cryptographic key sharding to distribute private key material across multiple components, ensuring no single entity has complete access to your wallets.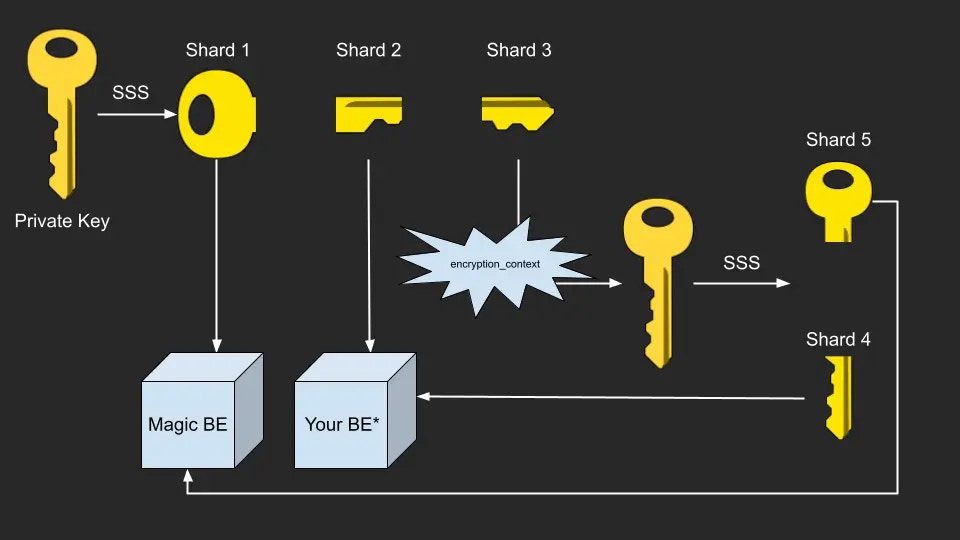
How Key Sharding Works
When a wallet is created, the private key is split using a 2-of-3 threshold scheme:Shard 1 (Magic)
Always available from Magic’s secure infrastructure. Used for all key operations including recovery.
Shard 2 (Recovery Key)
Returned to your application. Store securely in your database. Used only for wallet recovery when
encryption_context is lost.Shard 3 (Encrypted)
Encrypted with your
encryption_context and split into Shards 4 & 5. Required for all non-recovery operations.Shard 4 (Access Key)
Returned to your application. Store securely in your database. Combined with Shard 5 to recreate Shard 3.
Shard 5 (Magic)
Always available from Magic’s secure infrastructure. Used with Shard 4 to recreate Shard 3.
Operation Types
Non-Recovery Operations (Signing transactions, messages)- Uses: Shard 1 + Shard 3 (recreated from Shards 4 + 5 +
encryption_context) - Requires: User’s
encryption_context+ storedaccess_key
encryption_context is lost)
- Uses: Shard 1 + Shard 2
- Requires: Stored
recovery_key - Updates: All shard values with new
encryption_context
Custodial vs Non-Custodial Implementation
The implementation type depends on how you manage theencryption_context:
Non-Custodial Approach:
encryption_contextis derived from user input (e.g., passphrase, biometric data)- User must provide
encryption_contextfor each operation - Application cannot perform operations without user consent
encryption_contextis managed by your application- Application can perform operations on behalf of users
- Requires careful consideration of user consent and regulatory compliance
Implementation Patterns
Wallet Generation Flow
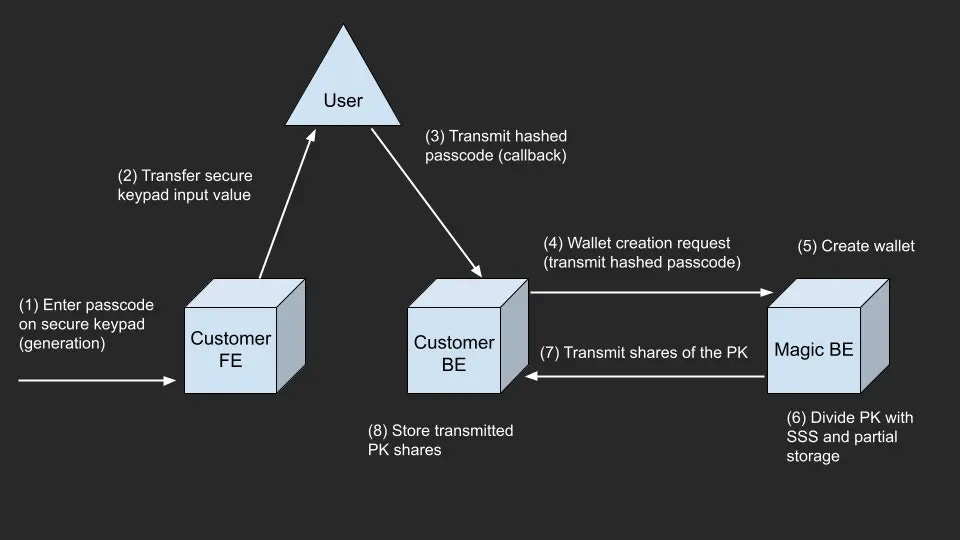
encryption_context:
- Client: User enters passphrase/biometric data
- Client: Hash the user input to create
encryption_context - Client: Send
encryption_contextto your server - Server: Call Core API to create wallet with
encryption_context - Server: Store
access_keyandrecovery_keysecurely - Client: Display wallet address to user
Non-Recovery Key Operation Flow
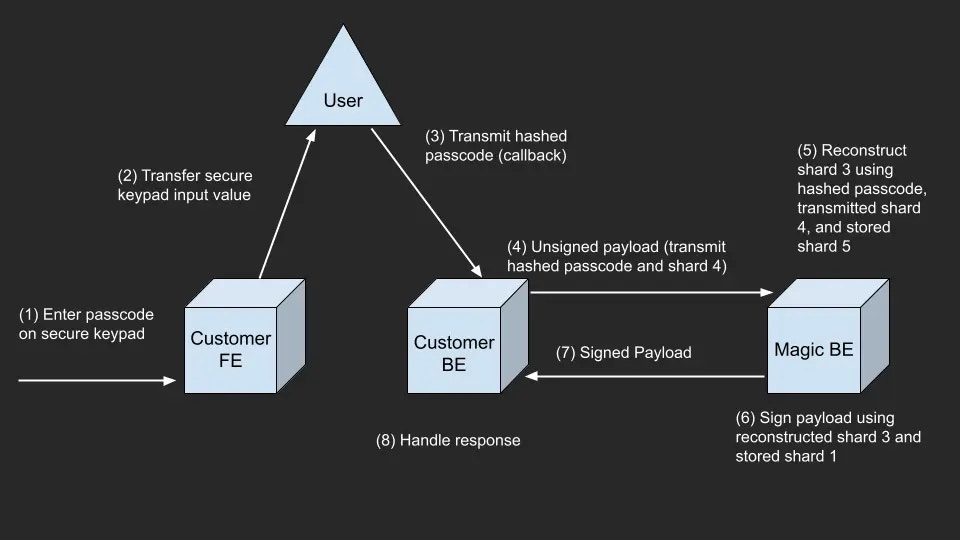
encryption_context:
- Client: User initiates transaction (e.g., transfer tokens)
- Client: User re-enters passphrase/biometric data
- Client: Hash the user input to recreate
encryption_context - Client: Send transaction +
encryption_contextto server - Server: Retrieve stored
access_keyfrom database - Server: Call Core API to sign transaction
- Server: Broadcast signed transaction to blockchain
Recovery Flow
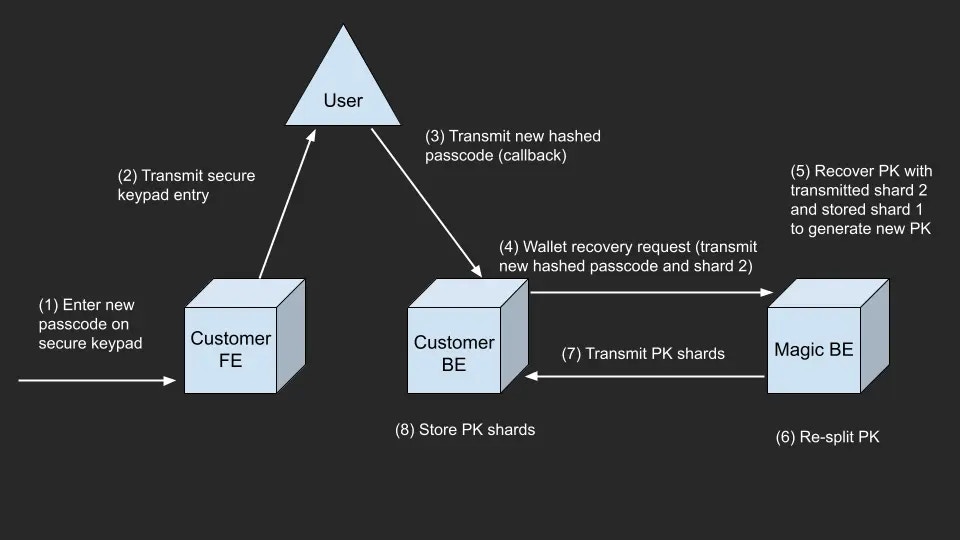
encryption_context is lost:
- Client: User indicates they’ve forgotten their passphrase
- Client: User enters new passphrase/biometric data
- Client: Hash the new input to create new
encryption_context - Client: Send new
encryption_contextto server - Server: Retrieve stored
recovery_keyfrom database - Server: Call Core API recovery endpoint
- Server: Update stored keys with new
access_keyandrecovery_key